Meraki MX Firewalls are an excellent choice for nonprofits looking to reduce IT costs and save internal resources. They offer advanced security features, cloud-based management, and easy deployment. However, it's essential to configure the Meraki MX Firewall correctly to ensure optimal performance and security. In this blog post, we will cover IT people's common configuration mistakes when setting up and configuring Meraki MX firewalls and how nonprofits can fix them.
1. Not Configuring the WAN Interface Correctly
One of the most common configuration mistakes is incorrectly configuring the WAN interface. This can cause issues with Internet connectivity and prevent the firewall from functioning correctly. Nonprofits should ensure the WAN interface is configured with the correct IP address, subnet mask, gateway, and DNS servers.
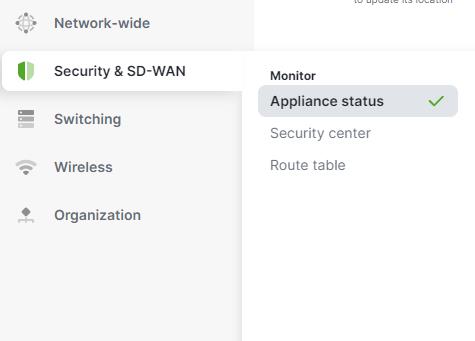
To configure the WAN interface, navigate to the "Security & SD-WAN " tab, and select "Appliance Status".
Then click on the "Uplink" tab. The WAN interface can be configured by selecting the edit (pencil) button to the right of the WAN section. Once the pencil is selected, the interface can be configured for DHCP to obtain an IP address dynamically or for a static IP to configure the IP address manually.
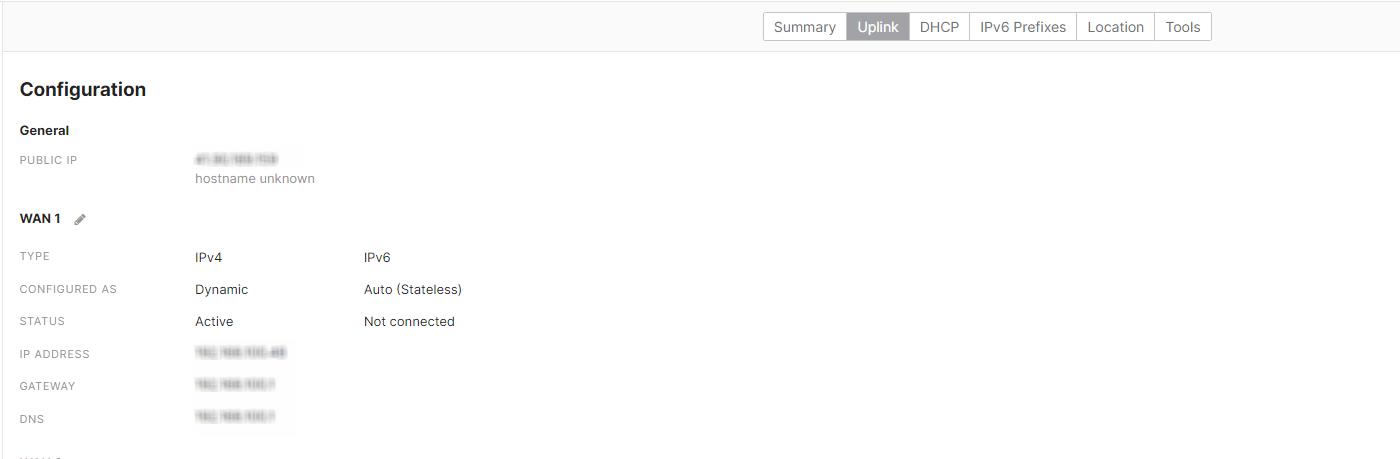
Nonprofits can set the IP address, subnet mask, gateway, and DNS servers.
After configuring the WAN settings, test the connectivity to ensure everything is working as expected. Use tools like ping tests and traceroutes to diagnose and troubleshoot any issues.
2. Not Configuring VPN Correctly
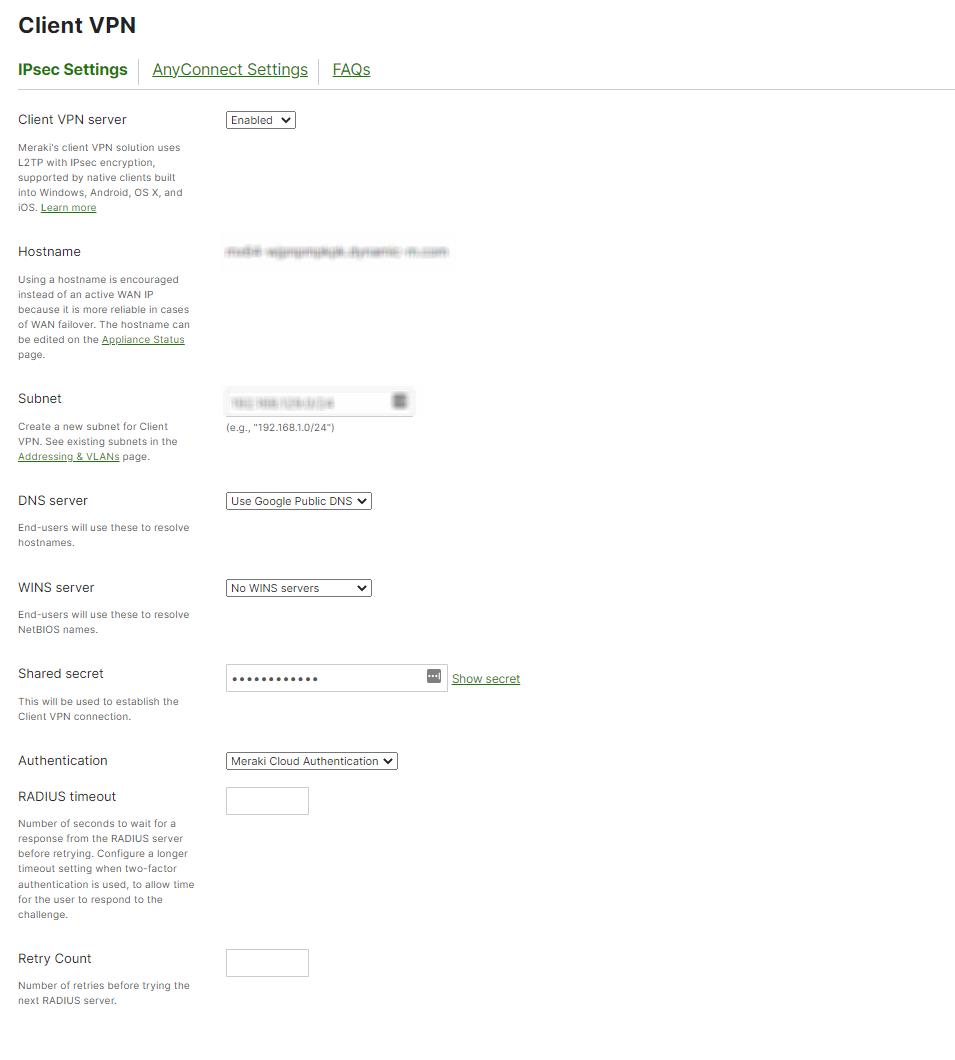
Misconfiguring VPN settings can cause issues with remote access and site-to-site connectivity. To fix this, nonprofits should ensure the VPN configuration is correct, including the authentication method, encryption, and subnet settings. Additionally, they should ensure that the firewall rules are configured correctly to allow VPN traffic.
To configure VPN settings, navigate to the "Security appliance" tab, select "VPN," and click on the "Site-to-site VPN" or "Client VPN" tab. Here, nonprofits can configure the VPN settings and the firewall rules to allow VPN traffic.
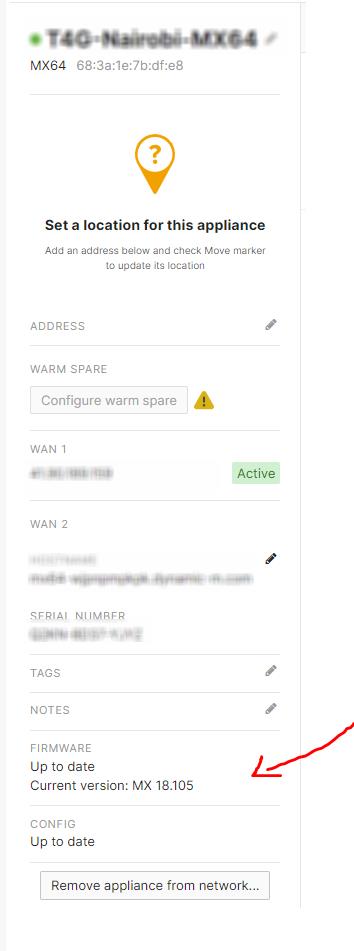
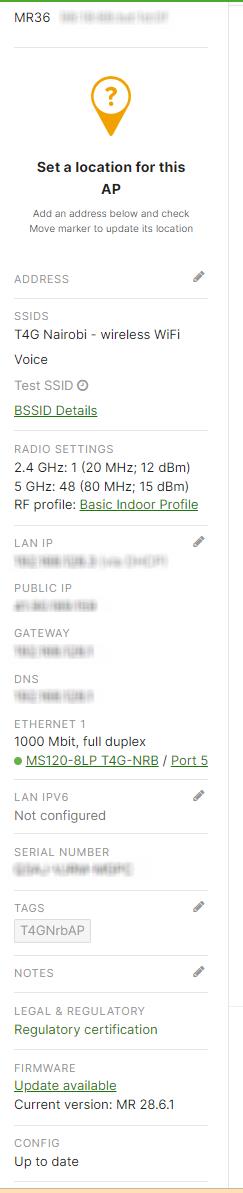
3. Not Updating Firmware
Failure to update the firmware can lead to security vulnerabilities, bugs, and other issues. Keeping the firmware up to date is crucial to ensure the firewall runs smoothly. Navigate to the "Security appliance" tab, select "Appliance status," and check for available firmware updates. They should then apply the updates as necessary.
The process is the same for the wireless access points and the switches.
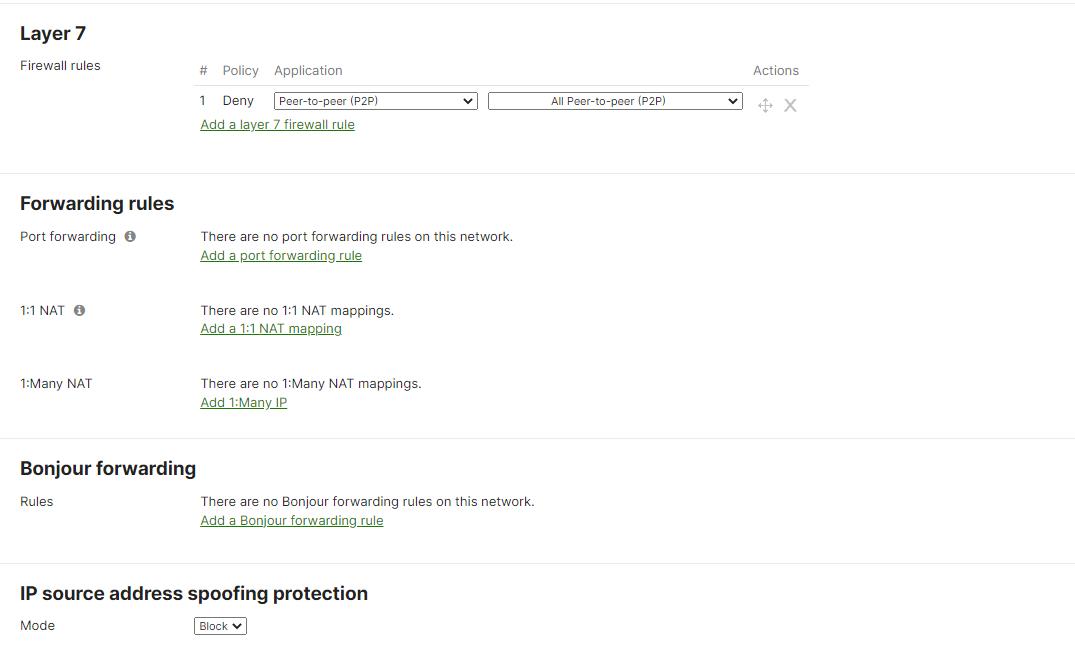
4. Misconfiguring Firewall Rules
Misconfigured firewall rules can result in either allowing too much or too little traffic. You should review the firewall rules and ensure they are configured correctly to allow the necessary traffic to pass through and block any unwanted traffic.
To configure layer 3 and layer 7 firewall rules, navigate to the "Security appliance" tab, select "Firewall," and click on the "Configure firewall" button. Here, nonprofits can create, modify, and delete firewall rules.
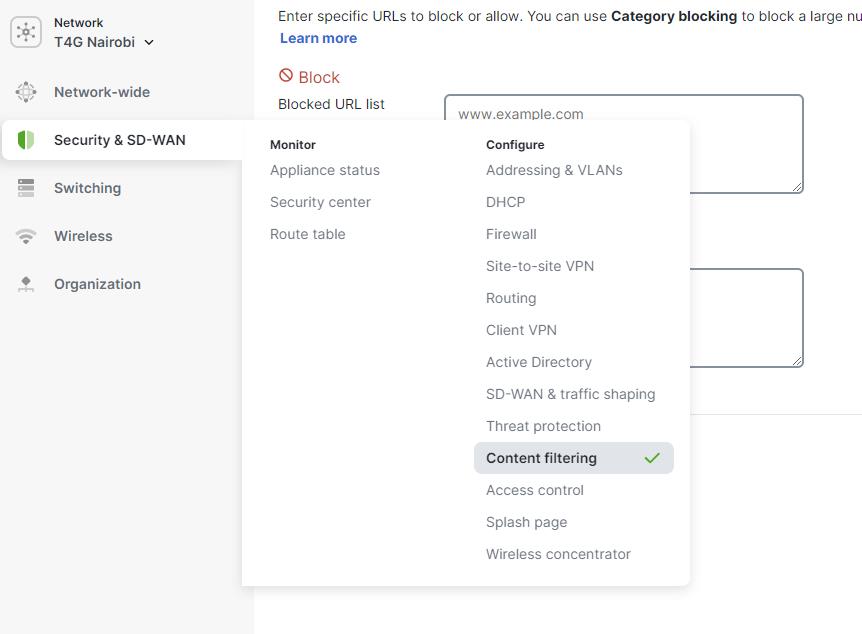
5. Not Configuring Content Filtering
Content filtering can help prevent users from accessing harmful or inappropriate content. Not configuring this can expose the network to potential security risks. To fix this, nonprofits should enable and configure content filtering to block access to unwanted content.
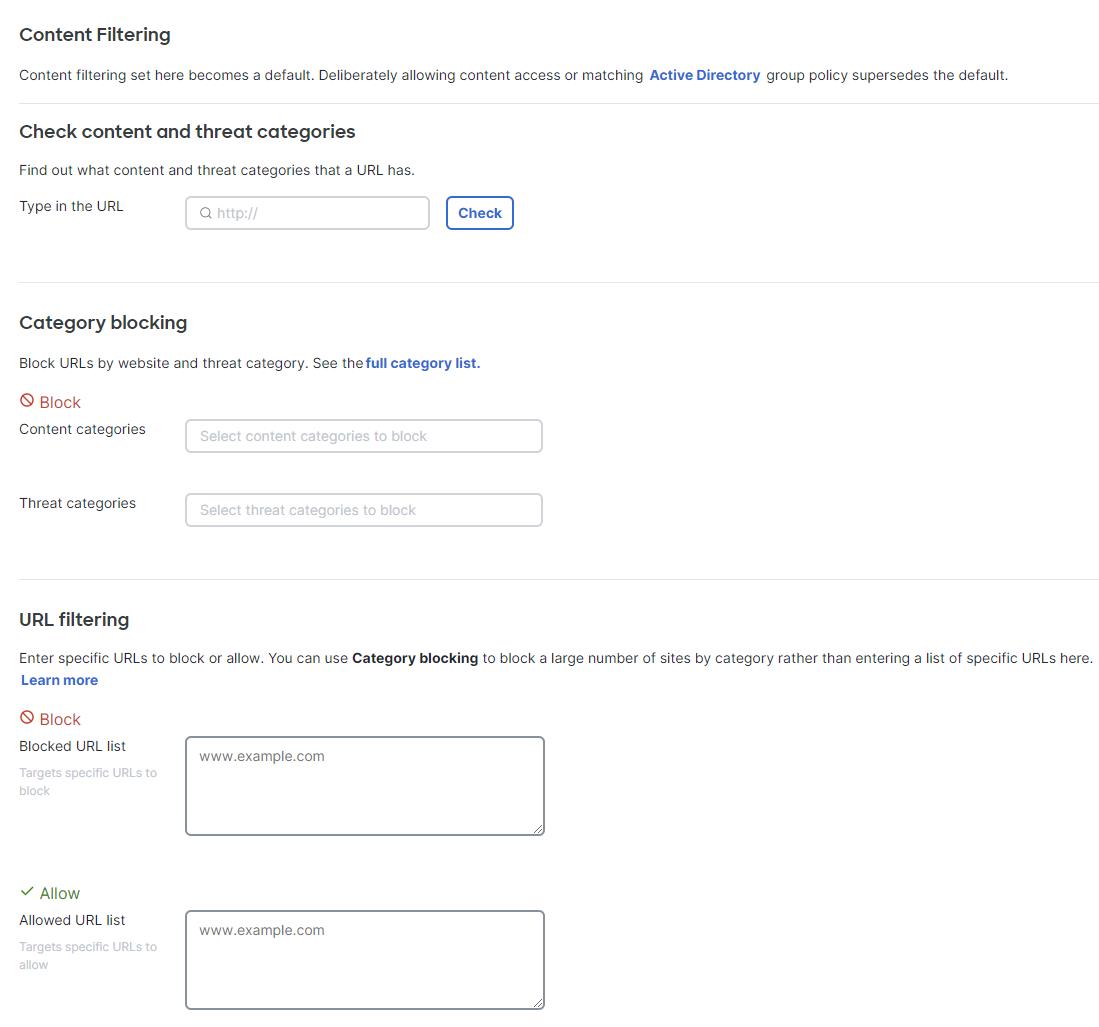
To configure content filtering, navigate to the "Security & SD-WAN" tab, and select "Content filtering, " From this page, you can check content and threat categories and perform category blocking, URL filtering, and search filtering. Nonprofits can enable content filtering and configure the settings to block unwanted content.
6. Not Using VLANs Correctly
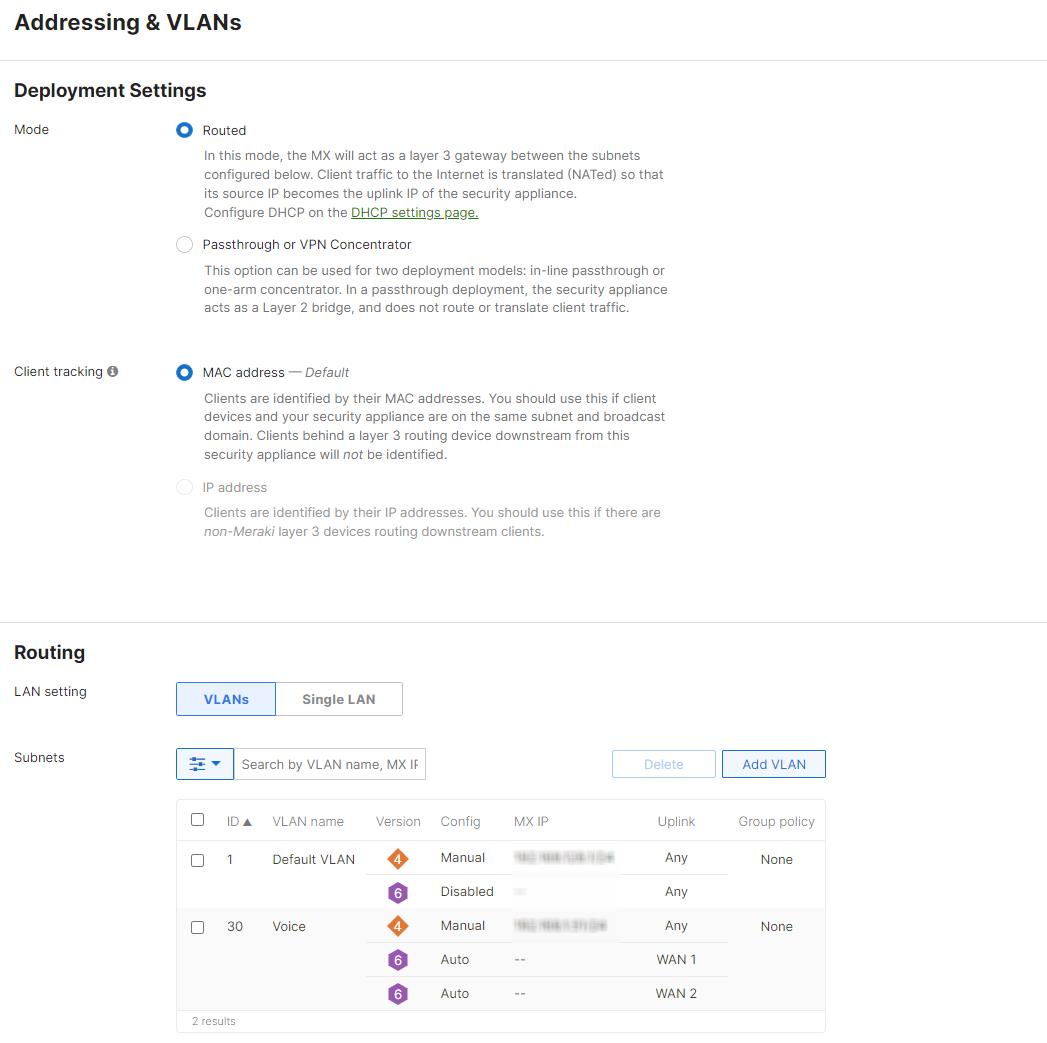
VLANs can be used to separate network traffic and improve security. Not using them correctly can result in security issues and network performance problems. Nonprofits must create VLANs and configure them correctly to ensure that traffic is separated as intended.
To configure VLANs, navigate to the "Security & SD-WAN" tab, select "Addressing & VLANs," and click on the "VLANs" tab. Here, nonprofits can create VLANs and configure them to separate network traffic.
7. Misconfiguring NAT Rules
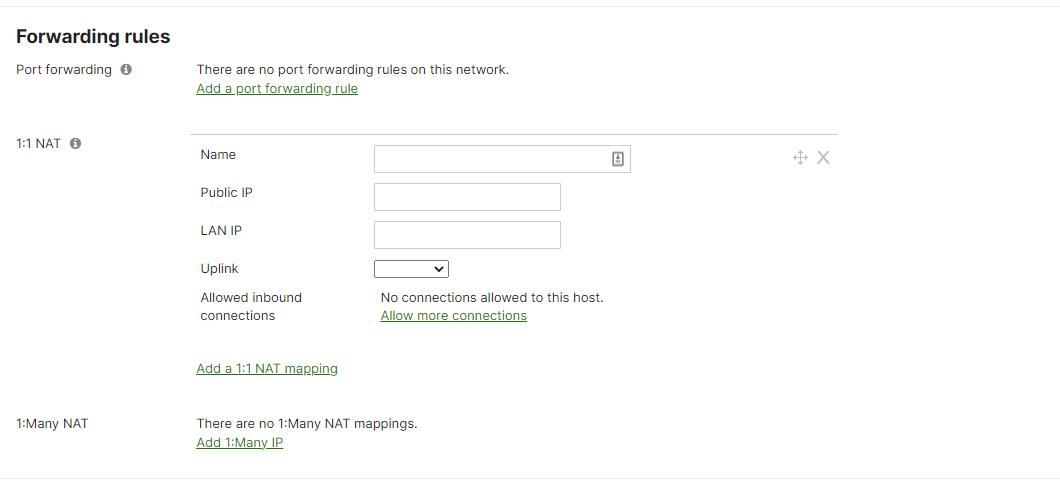
Misconfigured NAT rules can cause issues with inbound and outbound traffic. To fix this, nonprofits should review the NAT rules and ensure they are configured correctly to allow the necessary traffic to pass through the firewall.
To configure NAT rules, navigate to the "Security & SD-WAN" tab, and select "Firewall, " Under "Forwarding rules," you should see the 1:1 NAT rules section. Here, nonprofits can create, modify, and delete NAT rules.
8. Not Enabling Intrusion Prevention
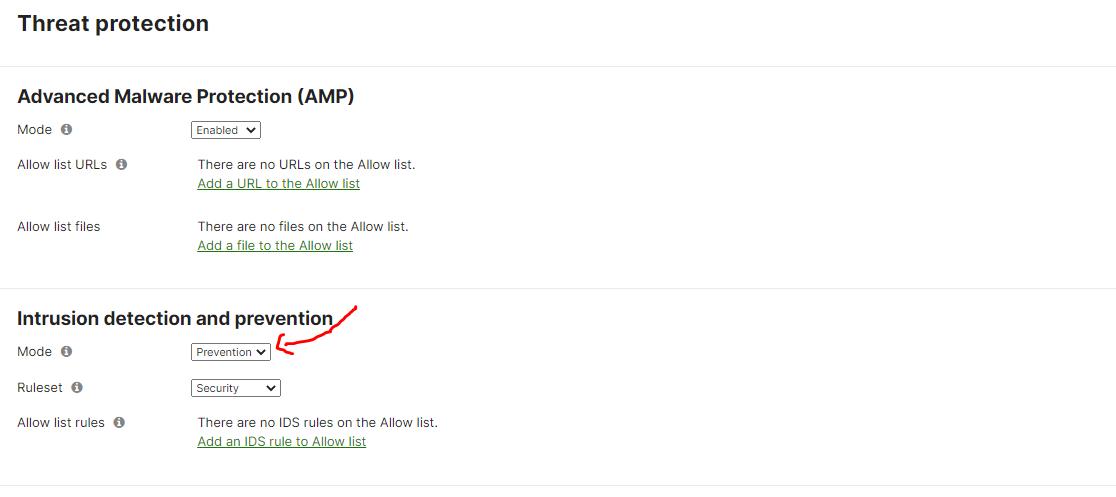
Intrusion prevention can help prevent attacks and other security risks from penetrating the network. Not enabling this feature can leave the network vulnerable to potential threats. It's crucial to enable intrusion prevention and configure it to best fit the organization's security needs.
To enable intrusion prevention, navigate to the "Security & SD-WAN" tab and select "Threat protection, " Here, nonprofits can enable intrusion prevention and configure the settings to fit their security needs.
9. Not Configuring SNMP Settings
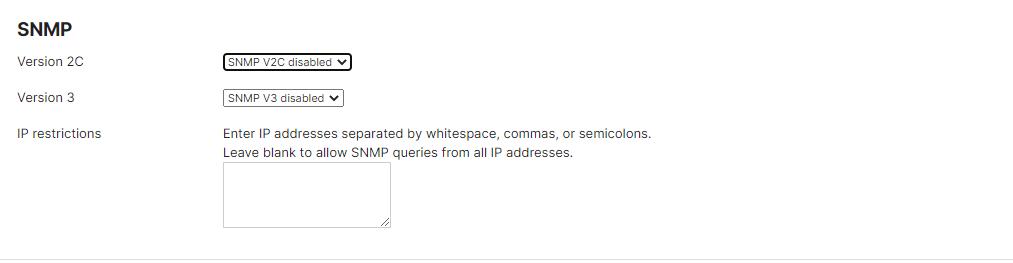
SNMP (Simple Network Management Protocol) monitors network devices and traffic. SNMP also allows network administrators to query devices for various information. Not configuring SNMP settings can make monitoring the firewall and diagnosing potential issues difficult. Nonprofits should enable SNMP and configure the settings as needed for monitoring purposes.
To configure SNMP settings, navigate to the "Organization" and "Organization settings tabs". Here, nonprofits can enable SNMP and configure the settings for monitoring purposes.
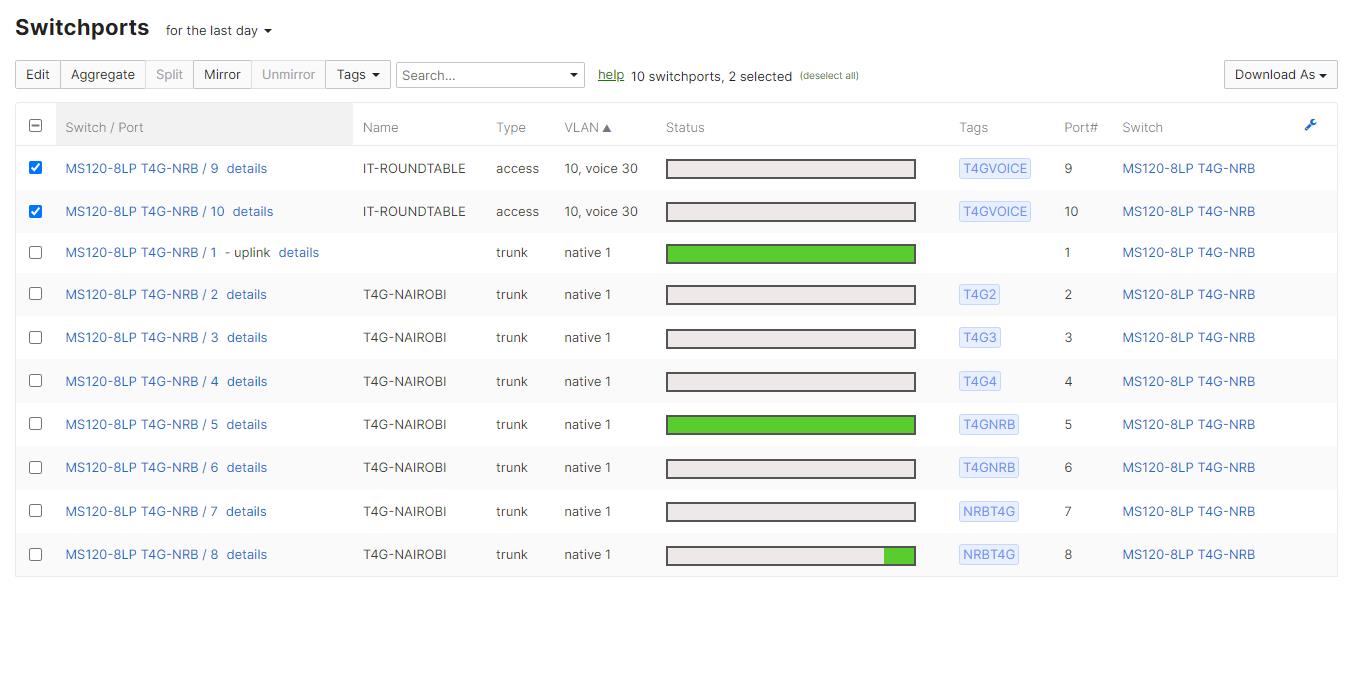
10. Not Configuring Link Aggregation
Link aggregation can be used to improve network performance and redundancy. Not configuring this feature can result in a bottleneck and network downtime in the event of a link failure. To fix this, you should configure link aggregation and ensure it functions properly.
To configure link aggregation, navigate to the "Switching"- "Monitor" – "Switch ports" tab, select any two ports, and click on the "Aggregate" tab. Here, nonprofits can configure link aggregation and ensure it functions properly.
Meraki MX Configuration Mistakes Conclusion
In conclusion, following these steps, nonprofits can avoid common configuration mistakes when setting up and configuring Meraki MX firewalls. By doing so, they can ensure their network is secure and functioning optimally.
Telecom4Good has certified Meraki engineers on staff to support our nonprofit clients with set up and configuration to ensure their Cisco Meraki networks are optimized for their operations. This support is at no cost to our clients. Please schedule a call or email us at meraki-support@telecom4good.org to learn more.

